MVC Example
Follow the steps below to add AuthorizationHub to an MVC web application.
Create Project & Install Packages
For this example, we'll be creating an MVC Razor based web application. It's called MVC_Razor_Example, and it's available on GitHub for you to reference. The application will need to implement authentication, so we'll choose Individual Accounts as the authentication type when creating the solution.
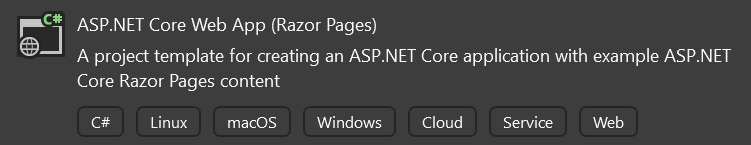
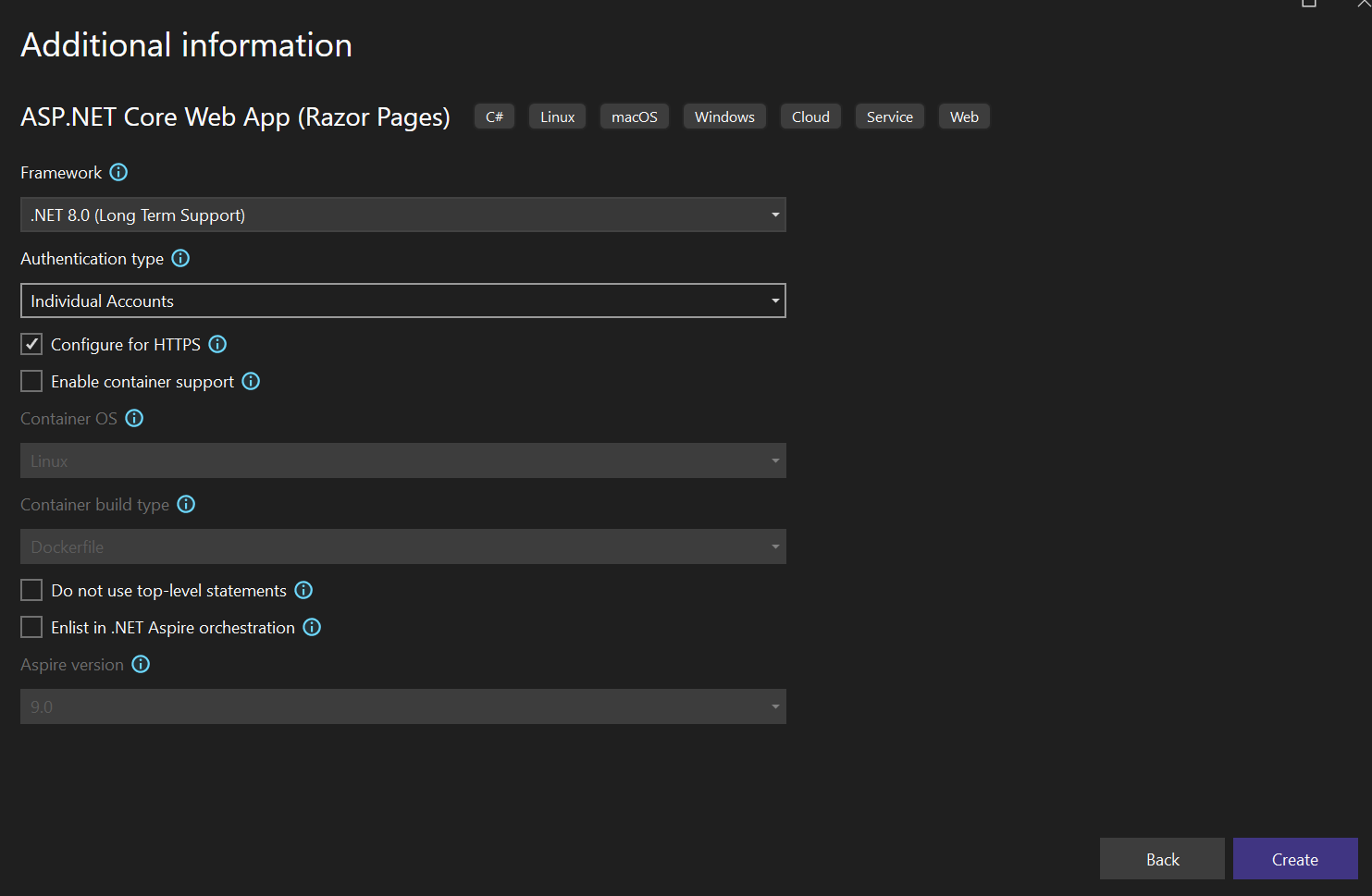
The next step is going to be to add the AuthorizationHub nuget packages. Currently AuthorizationHub is in prerelease, so if you add the Nuget packages with the Visual Studio UI, don't forget to check the include prerelease box so AuthorizationHub packages will be displayed.
AuthorizationHub contains custom authorization requirements for AuthorizationHub, along with the Claims Transformations that turn organizational tree relationships into claims for users.
AuthorizationHub.UI contains REST endpoints and a React user interface for you to interact with AuthorizationHub data.
AuthorizationHub.Data.SQL enables you to store data in a SQL Server database. AuthorizationHub.Data.Postgres enables you to store data in Postgres database. AuthorizationHub.Data.Sqlite enables you to store data in a local file using Sqlite.
For this exercise will use SQL Server.
Prepare Startup
After installation, update your Program.cs file:
using AuthorizationHub;
using AuthorizationHub.Data.SqlServer;
using AuthorizationHub.UI.Extensions;
var builder = WebApplication.CreateBuilder(args);
// Add services to the container.
var connectionString = builder.Configuration.GetConnectionString("DefaultConnection") ?? throw new InvalidOperationException("Connection string 'DefaultConnection' not found.");
builder.Services.AddDbContext<ApplicationDbContext>(options =>
options.UseSqlite(connectionString));
builder.Services.AddDatabaseDeveloperPageExceptionFilter();
builder.Services.AddDefaultIdentity<IdentityUser>(options => options.SignIn.RequireConfirmedAccount = true)
.AddEntityFrameworkStores<ApplicationDbContext>();
builder.Services.AddRazorPages();
// Sets up DI and needed authorization policies.
builder.Services.AddAuthorizationHub();
// Configures AuthorizationHub to use SQL Server
builder.Services.AddSQLServerToAuthorizationHub();
var app = builder.Build();
// Configure the HTTP request pipeline.
if (app.Environment.IsDevelopment())
{
app.UseMigrationsEndPoint();
}
else
{
app.UseExceptionHandler("/Error");
// The default HSTS value is 30 days. You may want to change this for production scenarios, see https://aka.ms/aspnetcore-hsts.
app.UseHsts();
}
app.UseHttpsRedirection();
app.UseStaticFiles();
app.UseRouting();
app.UseAuthorization();
app.MapRazorPages();
app.UseAuthorizationHubUI();
app.Run();
Configuration Data
Configuration data is stored in the app.config file, in a section called "AuthorizationHubOptions". You need to provide a connection string to the database, user ids for anyone who should be an administrator, and a license key.
We need a way to tell AuthorizationHub who the administrators are before the application has ever started. It’s a chicken before the egg sort of problem. When a user logs into your application, AuthorizationHub will look to see if the user has a "NameIdentifier" claim. In the case of ASP.NET Core Identity, that value would be the "AspNetUsers.Id" field. If the value in that claim is found in the list of administrators in the app.config file, the user is given access to edit data in AuthorizationHub.
"AuthorizationHubOptions": {
"SqlServerConnection": "Server=localhost;Database=AuthorizationHub;User ID=;Password=;MultipleActiveResultSets=true;TrustServerCertificate=True",
"Administrators": [
"b52d1aef-cf08-41dc-8e39-be197be6874c",
"0478bd7d-9ae8-4657-8d58-2b418f00cab7",
"2e0c5e52-31d3-405f-b880-619e92c66047"
],
"ClaimsCacheDuration": 1000
}
The ClaimsCacheDuration setting allows you to specify how long a user's claims should be cached in the web application before going back to the database to get updated data. This setting is measured in milliseconds.
A license file will be needed to enable AuthorizationHub. Create a file in the web application project, and call it AuthorizationHub.lic. Take the license data you get from AuthorizationHub.com, and place it in the file. Don't forget to set the properties on the file, so it will be copied to the output directory. License date is a JWT with an expiration date. When your license is nearing expiration, a message will be displayed in the UI. Because it is a JWT, you can also decode the license file and view the expiration date.
